Turns out, 42 was a kernel bug
Everything here is built for experts — from the first capability to the last fault handler.

core
principles
Gapfruit OS addresses all seven properties of highly secured devices through a holistic, capability-based microkernel architecture built on the Genode Framework, enabling rational arguments as to why the system is trustworth
Strong Isolation
In Gapfruit OS each component runs in a strict sandbox with strong microkernel-enforced isolation to protect the application and data at runtime. Each component only receives access to the resources and services it absolutely requires. Gapfruit OS guarantees the isolation of components from the outside-in and inside-out This duality of isolation is essential, as it is sometimes unclear which stakeholder considers which component of a system as trustworthy.
Control over all Dependencies
Resource Distribution
A child's component depends on its parent, who provides its children with resources and establishes service connections to other components.
Service Topology
Components connect through a service-oriented architecture, which provides access to resources like networking or storage, ensuring strict access control with guaranteed confidentiality and integrity.
Software Dependencies
The transactional package manager manages binaries and libraries. It defines and verifies the SBoM, enabling safe, efficient updates and minimal overhead.
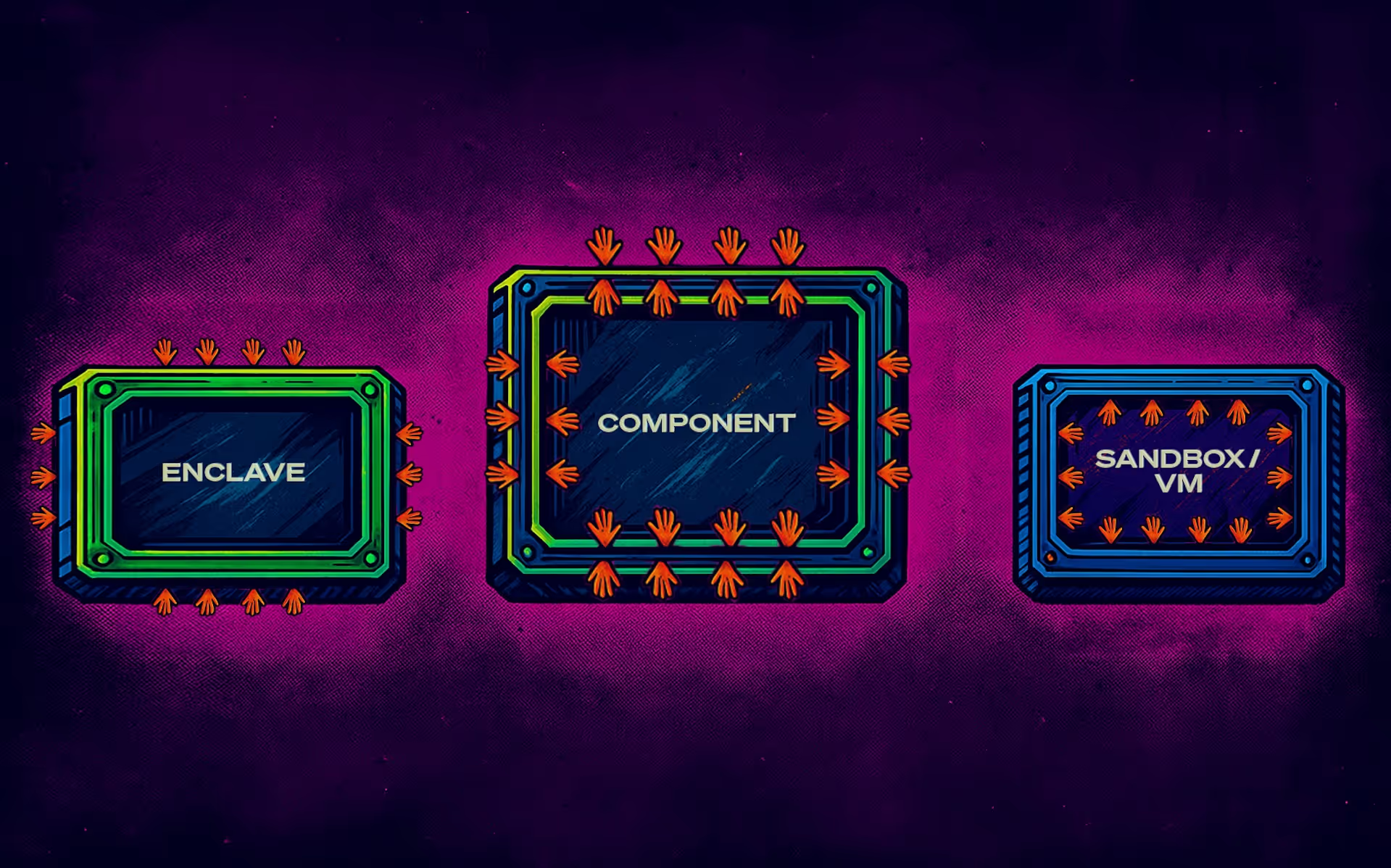
Attack Surface
In traditional systems, a network driver exploit can compromise the whole OS. Gapfruit OS isolates such drivers in userspace preserving system integrity and availability. With dynamic compartments and self-healing resiliency, the attack surface is reduced by over 99% compared to monolithic systems like Linux.
Resilience & Availability
Gapfruit OS provides self-healing resilience that automatically detects and recovers from faults to keep critical functions running without downtime. Components can be routed exclusively to specific CPUs, and resource limits have been enforced to ensure real-time performance and system stability
Device Driver Environment
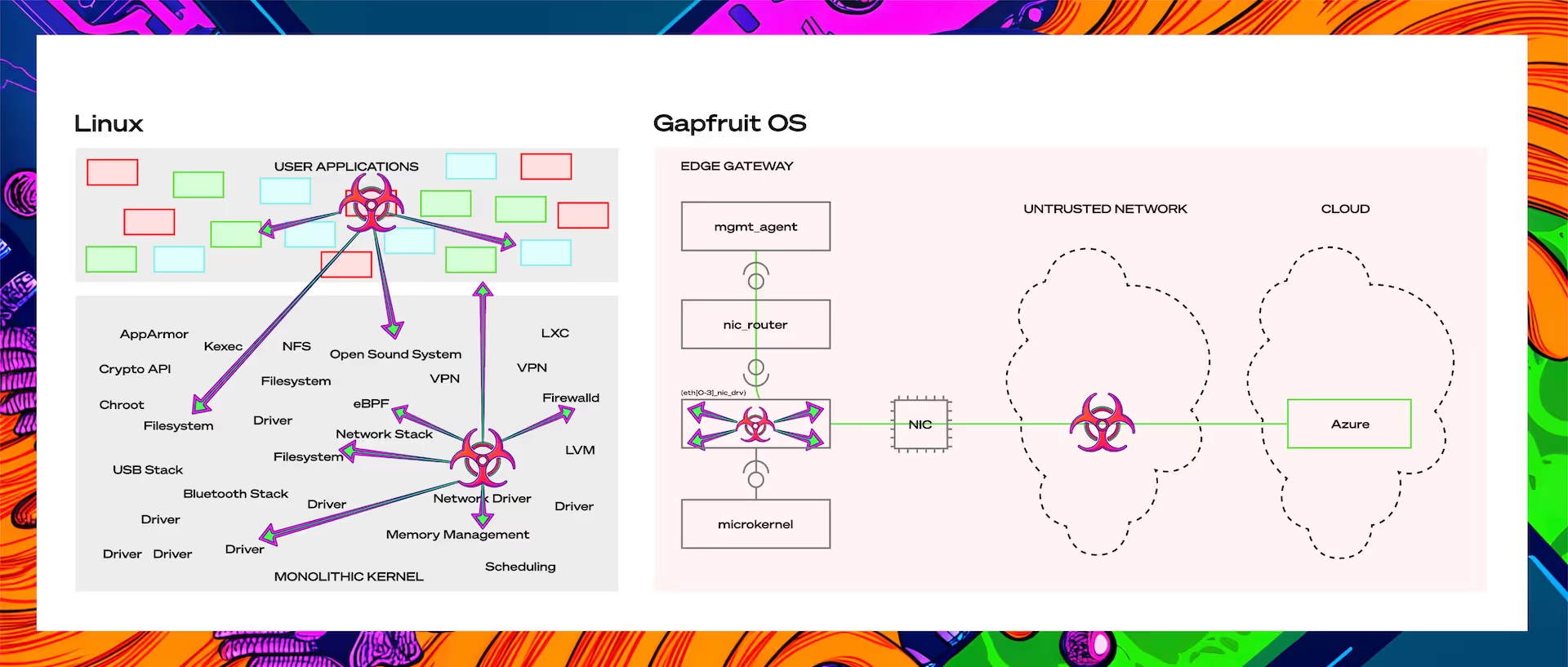
Gapfruit OS leverages the Linux Device Driver Environment (DDE) through user-space sandboxes from Genode, an absolute game-changer in the microkernel community. It enables Gapfruit to benefit from the vast Linux ecosystem and allows hardware compatibility without exposing the system to the typical risks of kernel-level Linux drivers.
TPM & PKI
Gapfruit enables application engineers to leverage the benefits of PKI in combination with strong digital identities (e.g. TPM) without requiring them to be security experts. Gapfruit OS utilizes TPM as a hardware root of trust for:
Why it works
no magic. just architecture.
Security
An exploit in the network stack in traditional OSs often compromises the entire system — one exploit, full control.
In Gapfruit OS, the same driver runs strictly isolated in the userspace. The vulnerability still exists, but it cannot take effect and becomes just another untrusted hop in the network, see pic X.
Sсalability
In traditional systems, every new device adds IT overhead — scripts, patching, manual ops. Gapfruit OS provides devices that are self-contained digital twins, not loosely managed agents
Availability
In traditional systems, one faulty driver or misbehaving component can take down the system.
Gapfruit OS self-healing resilience monitors every component — and restarts them safely when needed.
In a live demo, a misbehaving network driver was detected and restarted without downtime, and critical functions kept running.
Maintainability
Traditional systems rely on frozen BSPs and manual patching a nightmare in long product lifecycles. Gapfruit OS replaces this with a declarative, OTA-native model:
Our
Case Studies
Ready for EU Cyber Resilience Act (CRA): Secure Industrial Edge Gateways at Scale
Industrial digitalization often creates a deadlock between stakeholders
Practical Implementation Approach:
Gapfruit OS breaks this deadlock, bringing zero-trust principles directly to industrial environments. By pushing the last security perimeter closer to the devices, Gapfruit enables strong isolation between the data plane (sensors, actuators) and the management plane (updates, monitoring, control).
With Azure DPS and TPM-backed device attestation, gateways can be deployed with true plug-and-produce simplicity Managed through declarative tools like Device Lifetime Management, large-scale, zero-touch deployments become effortless.
Results
Factories can maintain productivity while securely connecting devices.
Machine builders can collect telemetry and comply with upcoming regulations like the EU Cyber Resilience Act.
Solution builders can focus on applications without handling low-level operation systems security.
Service providers can operate large fleets with low cost and high reliability.